My computer has been acting kind of sluggish and congested, my windows would take forever to open and it was almost impossible to browse websites or play any games – things would just take too long! So I figured maybe I had a virus or some malware on my computer affecting performance. I did a search for a free PC performance analyzer, one that would also scan my computer for malware. I came across Reimage through a recommendation in a forum and it did just that.
My computer has been acting kind of sluggish and congested, my windows would take forever to open and it was almost impossible to browse websites or play any games – things would just take too long! So I figured maybe I had a virus or some malware on my computer affecting performance. I did a search for a free PC performance analyzer, one that would also scan my computer for malware. I came across Reimage through a recommendation in a forum and it did just that.
You download the program and after it’s done compiling information on your PC (like which operating system you’re using), the preliminary scan begins.
Reimage first scans your computer thoroughly; all the files, folders, registry keys and values, drivers, DLL files, everything related to PC performance, etc. The free scan is done in only 5 minutes then you get your free PC scan summary.
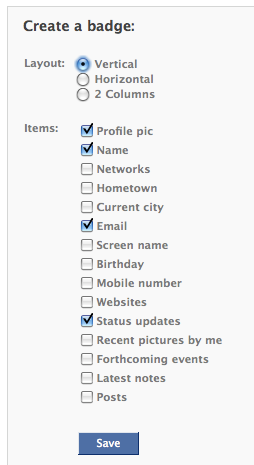
Reimage will scan your PC for:
PC Stability –Compiles a graph depicting which programs on your PC crash the most often.
PC Security - Scans for malware threats and uses 3 different ways of checking if your files are indeed a threat to your PC’s security. It then lists all the malicious files it’s found. These files are “tagged” for repair during the repair step.
In my case, Reimage found 5 malicious files on my PC. It also told me about one program that may crash.
PC Hardware - You get a hardware profile of your PC’s parts. It then compares your PC’s hardware (memory, disk space, CPU temperature) to a worldwide average.
In my case, I didn’t have enough memory on my PC (I guess I’ll just have to delete some programs I’m not using.)
I went ahead and purchased a license key to start the repair.
The Reimage repair started by clearing all the faulty files they found on my PC during the scan.
Then it was on to repairing damaged files and installing the fresh files from Reimage’s up to date online database. These files are downloaded straight from their servers (based on my geo-location) and are chosen based on my exact Windows operating system.
After the new replacement files were downloaded to my PC, the stability check took the longest to complete. The stability check makes sure that all performance issues are resolved on your PC. This is done by comparing your now fixed PC to the original stability report.
I was prompted to reboot a few times and then it was done. My computer’s performance has improved; I think cleaning out all those junk files, viruses and repairing damaged files gave my PC a real boost.